Introduction Aircrack-ng
Most people have terrible passwords, and Wi-Fai is no exception. Your Wi-Fai password is your primary line of defense against unwanted access to your network. That access can result in a whole host of other nasty things because an attacker can monitor the traffic on your network and even gain direct access to your computers. The best way to prevent such an intrusion is to use the same tools an attacker would to test the security of your Wi Fai password.
Conventions Aircrack-ng
- # – requires given linux commands to be executed with root privileges either directly as a root user or by use of
sudo command - $ – requires given linux commands to be executed as a regular non-privileged user
sudo commandInstall Aircrack-ng
This guide is going to use the Aircrack suite of tools. They’re already installed on Kali, so you won’t have to do anything. If you’re on another distro, they’re in your repositories.
$ sudo apt install aircrack-ngScan For Your Network
First, find out what the name of your wireless interface is with ip a. Once you have it, you can use airmon-ng to create a virtual monitoring interface on it.
$ sudo airmon-ng start wlan0The result of the command will give you the name of the new virtual interface. It tends to be mon0.
Dump the results of the monitor into a terminal, so you can see them.
$ sudo airodump-ng mon0You can see a table of data pertaining to wireless networks in your area. You only need information about your own network. Look for it, and note the BSSID and the channel that it’s on.
Dump The Results To A File
Next, you’re going to log the results of a scan to a file. That capture log will be needed by Aircrack to run a brute force attack on the network later. To get your capture, you’re going to run the same command as before, but you’ll specify your BSSID, channel, and the log location.
$ sudo airodump-ng -c 1 --bssid XX:XX:XX:XX:XX:XX -w Documents/logs/wpa-crack mon0Fill in your actual information before running the command, and leave it running.
Disconnect A Client
Open a new terminal. You’re going to use this one to disconnect one of the clients on your network. Take a look at the lower table in your other window running airodump-ng. It contains the BSSID of your network along with the BSSIDs of the clients. Pick one, and use the following linux command with that information.
$ sudo aireplay-ng -0 0 -c CLIENT BSSID -a NETWORK BSSID mon0You may need to add the --ignore-negative-one flag to the command.
That command will run indefinitely, continuously disconnecting that client. In the first line of the airodump-ng window, look for a message concerning a handshake to appear at the end of the line. It’ll be harder to see if you had to run --ignore-negative-one because a message about that will occupy the same space, causing the handshake message to flash for a second before being overwritten.
After only a couple of minutes, you can safely stop the disconnect requests and the dump. You can stop sooner if you see a handshake message.
Get A Wordlist
Brute force attacks run down a wordlist, testing each possibility. So, in order to carry one out, you’ll need a wordlist to test with. Kali Linux comes with a few already. If you’re on a different distro, you can find some online, but the best way to get them is from Kali. It’s worth loading a live CD or a VM just to pull them off.
On Kali, they’re located in /usr/share/wordlists. The one this guide will cover is rockyou.txt, but you can use any of the ones there.
If you really want to be obsessively thorough, you can use Crunch to create your own wordlists. Beware, they can be absolutely massive.
Attack!
Now that you have your wordlist and your capture, you’re ready to carry out the attack. For this one, you’ll be using the actual aircrack-ng command and passing it the wordlist and the capture.
$ sudo aircrack-ng -w rockyou.txt Documents/logs/wpa-crack-01.capIt can take a seriously long time to go through this list, so be patient. If you have a more powerful desktop, there’s nothing wrong with installing Aircrack on it, and transferring both files there.
When Aircrack finished, it’ll let you know if it found the password or not. If it did, it’s time to change your password.
Closing Thoughts
Remember this process should only ever be used to test your own security. Using it on someone else’s network is illegal.
Always use strong passphrases with as many characters as possible and include special characters and numbers. Avoid common dictionary words if possible.
What is Sniffing?
Sniffing is a process of monitoring and capturing all requests and data packets passing through a given network. Active Sniffing and Passive Sniffing are two types of sniffing.
What is Packet Injection?
Packet injection (also known as forging packets or spoofing packets) is a technique used in computer networking to interfere with an established network connection by creating packets that appear to be part of the normal communication stream. Packet injections are mostly utilized in Man-In-The-Middle (MITM) attacks, which we shall do during the deauthentication phase.
What is Network Interface Card (NIC)?
We can use wifi thanks to a network interface card. A network interface card is a piece of hardware that allows the computer to communicate with other computers across a network. It is a hardware component that is installed in a computer and enables a dedicated network connection to the machine. To see your NIC details, type the command below.
Note: My NIC is labeled as wlp1s0, yours may be different.
iwconfig 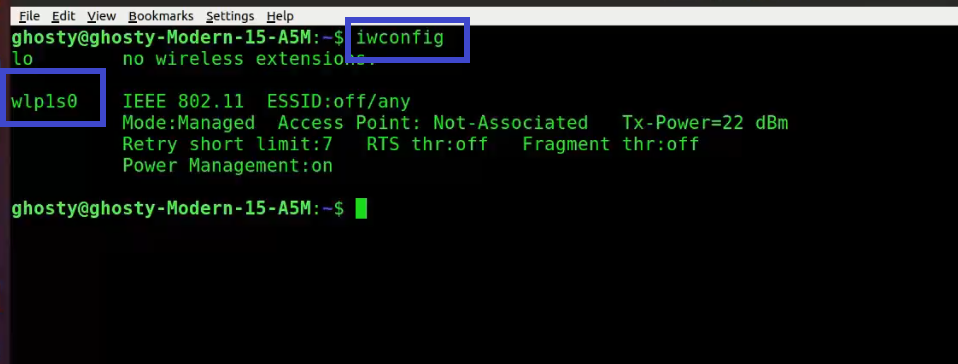
What is Aircrack-ng?
Aircrack-ng is a comprehensive set of tools for evaluating the security of WiFi networks. It focuses on various aspects of WiFi security, including:
- Monitoring: Packet capture and data export to text files for additional processing by third-party tools
- Attacking: Packet injection attacks include replay attacks, de-authentication, and the creation of bogus access points, among other things.
- Testing: Checking the capabilities of WiFi cards and drivers (capture and injection)
- Cracking: WEP and WPA PSK Cracking (WPA 1 and 2)
The tools are all command-line-based, allowing for a lot of scripting. A great variety of graphical user interfaces have made advantage of this feature. It is available for Linux, Windows, macOS, FreeBSD, OpenBSD, NetBSD, Solaris, and even eComStation 2.
We will be using the airmon-ng, airodump-ng, aireplay-ng, and Aircrack-ng tools from the Aircrack-ng suite. Let's look at their usage.
Airmon-ng: Monitor Mode
Airmon-ng is used to manage wireless extensions modes. To sniff a wireless connection, you must switch your wireless card from managed to monitor mode, which is done with airmon-ng. Monitor mode allows your card to listen in on all packets in the air. Normally, only packets intended for you will be "heard" by your card. We can later capture the WPA/WPA2 4-way handshake by listening to every packet.
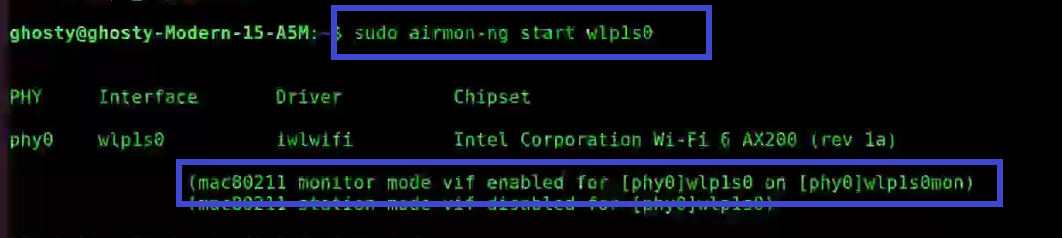
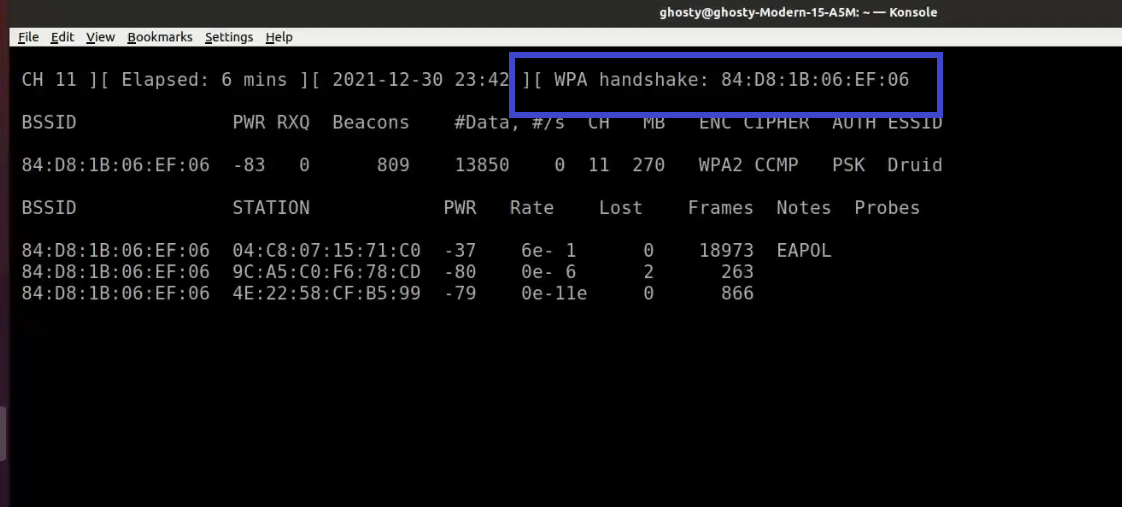
Airodump-ng: Authentication Handshake
Airodump-ng is a wireless sniffer that can collect data from several wireless Access Points. It's used to look for nearby Access Points and record handshakes.
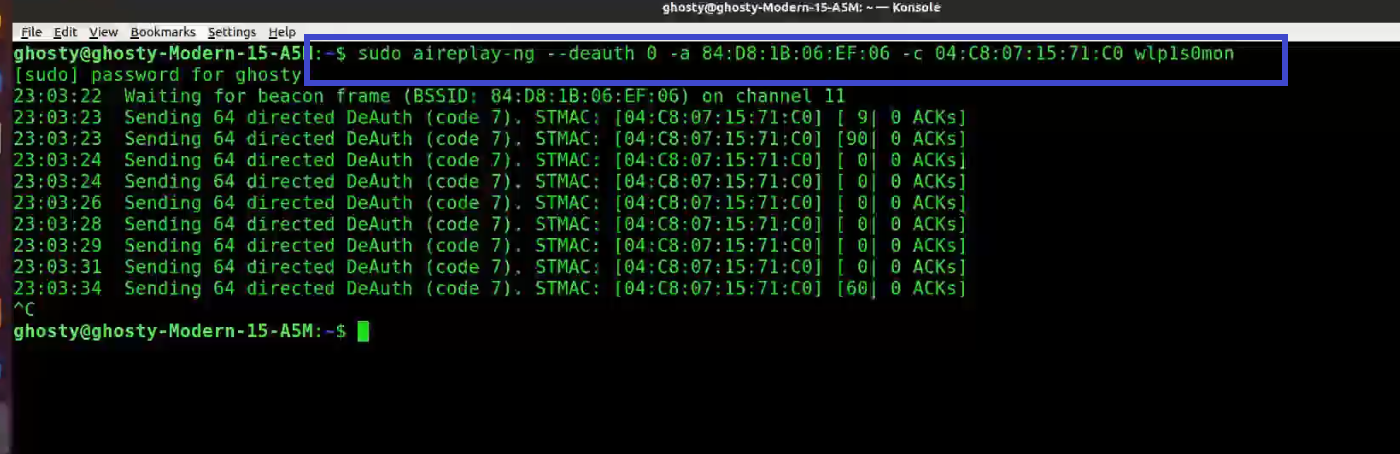
Aireplay-ng: Deauthenticate Client
Aireplay-ng is a replay attack and packet injector tool. Users can be de-authenticated from their APs in order to collect handshakes. This step is only required if you've decided to speed up the process. Another constraint is that the AP must be connected to a wireless client at this time. If no wireless client is currently connected to the AP, you must be patient and wait for one to connect before capturing a handshake. You can go back and repeat this step if a wireless client arises later and airodump-ng fails to capture the handshake.
Aircrack-ng
In order to find the key, Aircrack-ng is used to attack WPA/WAP2 wireless protocols. For cracking the password Aircrack-ng uses brute force attack against the captured handshake. The drawback of using Aircrack-ng to brute force is that it utilizes CPU instead of GPU which makes the attack slow.
Frequently Asked Questions
How do I earn money with affiliate marketing?
Who Can Be An Affiliate Marketing Program Seller?
How do I know what's popular?
How do I find products and companies to promote?
How do I promote affiliate products?
People are also reading:- Smartphone Circuit Diagram information.
- 10 Best Ethical Hacking Books for Beginner to Advanced Level. Best Online Teaching Platforms Name for Teachers
- Affiliate Marketing For Beginners to Advance Successful Strategy.
- Best Password cracking techniques used by hackers. Explanation
- How many types of darknet user software and website.
- What is PageMaker? PageMaker Introduction
- How to become an operations manager ? Build leadership skills.
- Popular Types of Information Systems and Their Applications
- Smartphone Circuit Diagram information.
- 10 Best Ethical Hacking Books for Beginner to Advanced Level. Best Online Teaching Platforms Name for Teachers
- Affiliate Marketing For Beginners to Advance Successful Strategy.
- Best Password cracking techniques used by hackers. Explanation
- How many types of darknet user software and website.
- What is PageMaker? PageMaker Introduction
- How to become an operations manager ? Build leadership skills.
- Popular Types of Information Systems and Their Applications







